Ransomware Unmasked: From WannaCry to LockBit
Ransomware has become a headline-making threat, disrupting hospitals, governments, and global enterprises. While many have heard the names WannaCry, Petya, or LockBit, fewer understand how these attacks evolved or what makes each of them significant. This article dives into the key ransomware variants that have shaped the cyber threat landscape—explained in plain terms for tech-aware readers without going too deep into the weeds.
What Is Ransomware, Really?
At its core, ransomware is malicious software that locks or encrypts files on a device, then demands a ransom to unlock them. It’s digital extortion. The usual goal? Money—paid in cryptocurrency like Bitcoin to maintain anonymity.
There are two major types:
- Locker ransomware: Locks you out of your device.
- Crypto ransomware: Encrypts your files so you can’t access them.
Now, let’s explore some infamous names that changed the game.
WannaCry: The Global Wake-Up Call (2017)
WannaCry was a watershed moment in cybersecurity. In May 2017, it exploded across 150 countries, taking down hospitals, telecoms, and banks in hours. It used a leaked NSA exploit called EternalBlue, which abused a vulnerability in Windows’ file-sharing system (SMBv1).
What made WannaCry terrifying wasn’t just the ransomware—it was its ability to spread automatically, like a digital worm. Machines didn’t have to click anything; if they were vulnerable, they got infected.
Why it mattered:
- Exposed how dangerous leaked government tools can be.
- Showed how quickly ransomware can spread without human action.
- Hit critical infrastructure, including the UK’s NHS.
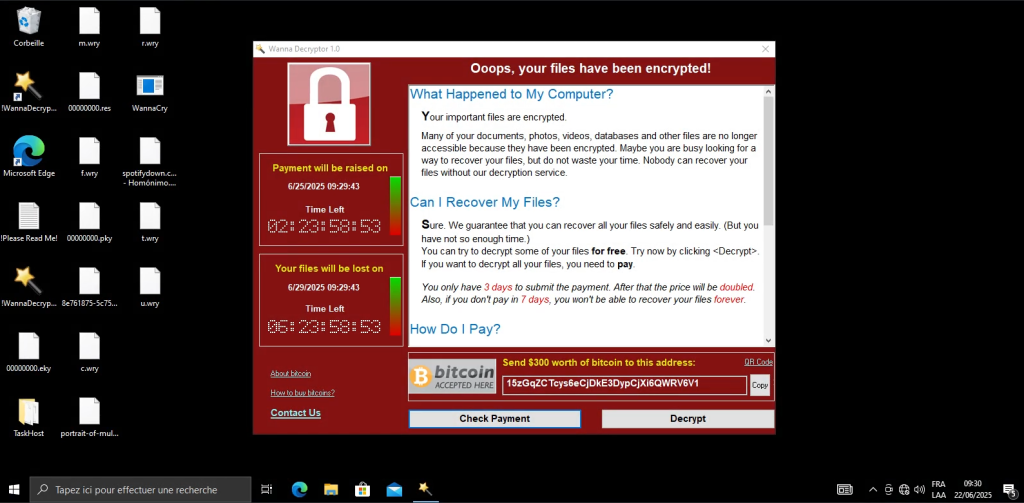
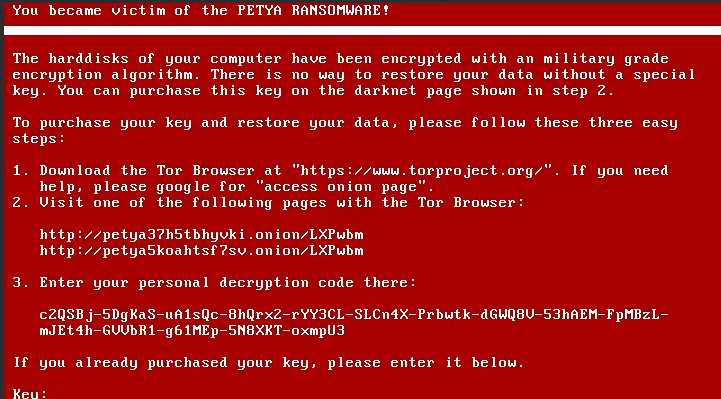
Petya / NotPetya: Ransomware Disguised as Cyberwarfare (2017)
Petya had been around before 2017, but NotPetya was something different. It looked like ransomware but behaved more like a cyberweapon.
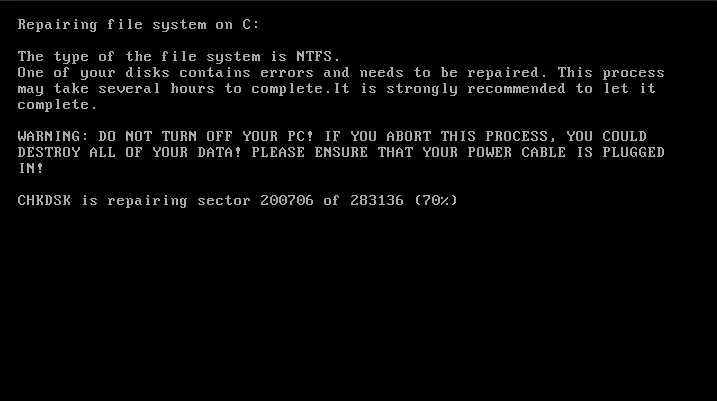
NotPetya also used EternalBlue, but unlike WannaCry, it wasn’t really about ransom. It destroyed data irreversibly, particularly in Ukrainian systems, and spread globally, affecting companies like Maersk and Merck.
Why it mattered:
- Demonstrated ransomware can be a smokescreen for sabotage.
- Showed how even “collateral damage” from cyberwar can hit multinationals.
- Reinforced the need for network segmentation and timely patching.
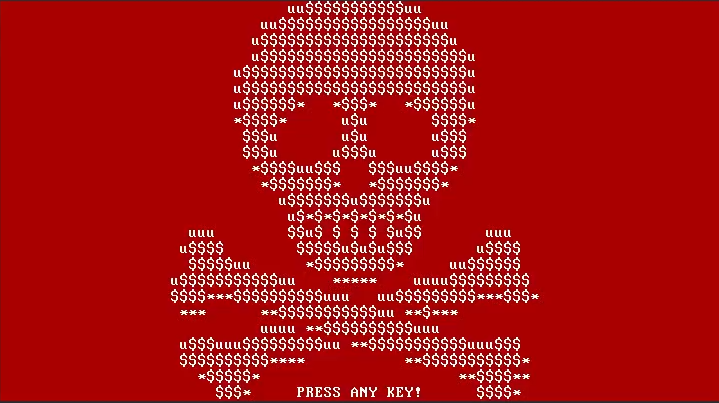
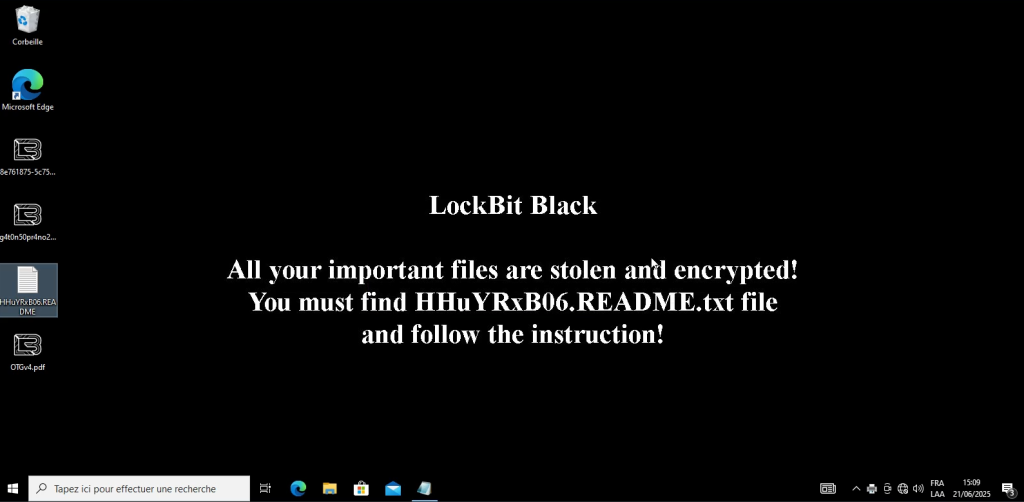
LockBit: The Modern Business Model of Ransomware
LockBit represents the current wave of Ransomware-as-a-Service (RaaS). In this model, the developers create the ransomware and lease it to affiliates who perform the attacks. Profits are split.
LockBit evolved rapidly from its initial release in 2019, with LockBit 2.0, 3.0, and newer versions introducing automation, anti-analysis features, and even “leak sites” where they publish victim data if no ransom is paid.
Why it matters:
- Professionalized cybercrime: LockBit has PR, bug bounties, and branding.
- RaaS makes attacks more accessible to less-skilled criminals.
- It’s currently among the most active ransomware families in the world.
Key Lessons
- Patching matters: WannaCry and NotPetya could’ve been stopped by applying a Microsoft patch released before the attacks.
- Backups save lives: Having offline, tested backups is the best defense against encryption-based attacks.
- Detection isn’t prevention: Once ransomware starts, damage is often immediate. Early detection tools help, but proactive defenses are crucial.
- Ransom ≠ Recovery: Paying doesn’t guarantee your data back—and it may fund more attacks.
Final Thoughts
Ransomware is no longer just about files and money—it’s about operational disruption, national security, and cybercrime at scale. From WannaCry’s global chaos to LockBit’s businesslike efficiency, these threats reveal a shifting landscape that blends hacking with organized crime.
Understanding ransomware isn’t just for IT departments anymore—it’s boardroom-level risk. The sooner organizations treat it that way, the better prepared they’ll be for the next headline-making attack.